Security
UiPath Security
UiPath products make your company better while maintaining focus on security
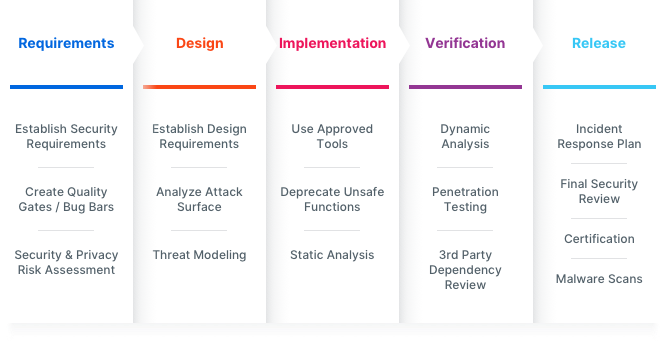
Every UiPath product is designed and developed with security in mind.Security is built directly into our development lifecycle, by performing both automated security scans and penetration tests.We submit our releases to independent third-party review at the highest level to ensure that our security is more than trusted.
Security governance and controls
UiPath maintains a comprehensive information security management system and engages independent auditors to provide industry-standard certifications and attestations.
Additional details regarding the UiPath technical and organisational measures are available in UiPath Information Security Exhibit.
UiPath defines information security related roles and responsibilities across the organisation from the executive management (CISO, CPO, CTO, CLO) to employees and contingent staff.
Industry Certifications and Attestations
UiPath works to improve quality and security standards and design an internal roadmap of assurance and standards relevant to, and adequate for, the industry in which UiPath operates.
ISO/IEC 27001:2013, ISO/IEC 27017:2015, ISO/IEC 27018:2019
UiPath has engaged a certification body accredited by the ANSI National Accreditation Board (ANAB) and United Kingdom Accreditation Service (UKAS) to audit UiPath’s information security management system (ISMS) annually for conformity with the ISO/IEC 27001:2013 standard and aligned to meet the control implementation guidance and additional control sets of ISO/IEC 27017:2015 and ISO/IEC 27018:2019. The corresponding certification has been issued, the scope of which is detailed therein.
ISO 9001:2015
UiPath has engaged a certification body accredited by the ANSI National Accreditation Board (ANAB) to audit UiPath’s quality management system (QMS) annually for conformity with the ISO 9001:2015 standard and issue the corresponding certification the scope of which is detailed therein.
SOC 1®
UiPath has engaged an independent certified public accounting firm to examine controls that may be relevant to a customer's internal control over financial reporting (ICFR) in accordance with American Institute of Certified Public Accountants (AICPA) System and Organizational Control (SOC®) 1 guidance.
SOC 2®
AICPA System and Organization Controls (SOC) reports provide independent assurance to global customers in highly regulated industries who trust UiPath with their most sensitive data.
UiPath has engaged an independent certified public accounting firm to examine controls relevant to American Institute of Certified Public Accountants (AICPA) Trust Services Criteria for security, availability, and confidentiality relevant to the UiPath cloud offerings and issue SOC 2® reports.
Current SOC 2® Type 2 report covers the design and operating effectiveness of controls relevant to UiPath Automation Cloud Platform, Action Center, AI Center, Apps, Automation Hub, Automation Ops, Computer Vision, Data Service, Document Understanding, Automation Cloud Robots - VM, Automation Cloud Robots - Serverless, Insights, Integration Service, Process Mining Cloud, Orchestrator, Studio Web, Task Mining, Test Manager, and Communications Mining.
Health Insurance Portability and Accountability Act (HIPAA)
Under HIPAA, UiPath acts as a business associate to covered entities and other business associates. HIPAA attestation provides independent assurance to customers and business partners that UiPath has designed and implemented administrative, physical and technical safeguards applicable to UiPath’s business as a cloud service provider.
UiPath has engaged an independent certified public accounting firm to examine UiPath’s information security and privacy program every six months for conformity with applicable implementation specifications within the HIPAA Security, Privacy, and Breach Notification Rules.
Current HIPAA Type 2 attestation covers the design of applicable administrative, physical, and technical safeguards relevant to UiPath Automation Cloud Platform, Action Center, AI Center, Apps, Automation Hub, Automation Ops, Computer Vision, Data Service, Document Understanding, Automation Cloud Robots - VM, Automation Cloud Robots - Serverless, Insights, Integration Service, Process Mining Cloud, Orchestrator, Studio Web, Task Mining (Assisted, Unassisted, and Workforce Intelligence), Test Manager, and Communications Mining.
HITRUST
HITRUST Risk-based, 2-year (r2) Certified status demonstrates that UiPath has met demanding regulatory compliance and industry-defined requirements and is appropriately managing risk. This achievement places UiPath in an exclusive group of organizations worldwide that have earned this certification.
Current HITRUST certification scope covers UiPath Automation Cloud Platform, Orchestrator, Insights, and Automation Hub.
FedRAMP
UiPath Automation Cloud Public Sector has achieved the Authorized status from the Federal Risk and Authorization Management Program (FedRAMP®). Available on the FedRAMP Marketplace, the UiPath Business Automation Platform can be used to securely and transparently process data, speed operations, and empower government workers. UiPath offers FedRAMP-certified core management, governance, analytics, idea capture and management, and support for self-hosted automations on-premises or in the cloud. UiPath also offers public sector agencies continuous testing capabilities for apps and automations.
IRAP
IRAP consists of a set of requirements listed in the Australian Government Information Security Manual (ISM) which is produced by the Australian Cyber Security Centre (ACSC). These requirements are assessed by an independent third party to evaluate our security posture. Rather than a certification or attestation, we receive a detailed report indicating compliant and ineffective controls, which Australian customers use to assess our SaaS security risks. Learn more here.
C5 (Cloud Computing Compliance Controls Catalogue)
C5 is a government-backed attestation framework, which was introduced in Germany by the Federal Office for Information Security (BSI). C5 helps companies demonstrate operational security against common cyber attacks within the context of the German government's "Security Recommendations for Cloud Providers" guidelines. C5 is a mandated requirement in Germany for those providing cloud services to government agencies, applicable to any service provider inside or outside of Germany. UiPath’s C5 Type 2 attestation demonstrates our commitment to providing security assurance and transparency to our German customers.
ENS (Esquema Nacional de Seguridad)
ENS is a set of security controls and standards that are required to be implemented by government agencies, public organizations, and service providers that process data for public services in Spain. Spain’s National Security Schema (ENS) establishes a uniform set of requirements, promotes continuous security management, and offers a reference for effective security posture. Under the Spanish Royal Decree 3/2010, ENS is a compulsory requirement for central government customers in Spain. UiPath has undergone an independent ENS audit report of UiPath Automation Cloud services.
National Health Service (NHS) Data Security & Protection Toolkit (DSPT) Self-assessment
UiPath UK Limited has submitted its 2022/2023 National Health Service (NHS) Data Security & Protection Toolkit (DSPT) self-assessment and exceeded standards. The DSPT allows organizations to measure performance against the UK National Data Guardian’s ten data security standards. Annual submission of the DSPT self-assessment provides assurance that UiPath is practicing good data security and that personal information is handled correctly.
Cyber Essentials
Companies undergoing annual Cyber Essentials audits help reduce the level of cyber security risk in the UK government supply chains. The Cyber Essentials scheme defines a set of controls which, when properly implemented, will provide organizations with basic protection from the most prevalent forms of threat coming from the internet. The scheme is mandatory for central government contracts advertised after 1 October 2014 which involve handling personal information and providing certain ICT products and services.
UiPath has engaged a certification body authorized by IASME to audit UiPath UK Limited annually against UK National Cyber Security Centre (NCSC) technical requirements for IT infrastructure and issue a Cyber Essentials certificate.
Paris Call for Trust and Security in Cyber Space
UiPath joined a global call for Nation States, Companies and Civil Society to come together and face the increasing threats endangering citizens and infrastructure in cyberspace. It is based around nine common principles to secure cyberspace and the commitment to adopt responsible behavior. Discover the 9 principles here.
Bug Bounty Program
UiPath Bug Bounty Program aims to leverage the expertise of HackerOne's ethical hacker community to find vulnerabilities in our RPA Platform and surrounding ecosystem in order to keep our customers, partners and community users safe from malicious activities.
If you find a vulnerability on any systems that you feel are part of the UiPath organization, please send us an email at hackerone@uipath.com.
The Program focuses on high priority items such as:
Identifying and exploiting vulnerabilities in the implementation of Orchestrator and Robot that will permit escalation of privileges and perform out of rights/bound actions on Orchestrator.
Identifying publicly discoverable/accessible service end-points for UiPath.
Discovering management level secrets such as passwords.
Gaining control over the Orchestrator machine(s) in an on-premise scenario where the threat actor (malicious entity) is not a provisioned user on Orchestrator at application layer or OS level but is able to join the network on which robot and Orchestrator is deployed.
Using manual analysis or tools to conduct an objective evaluation of the Orchestrator application against OWASP Top 10 2017 Application Security Risks.
Injecting or uploading executable code into Orchestrator application that eventually runs itself, via interactive methods or access through APIs.
Internal & external testing
Before every GA/Major release for our products, we run the following analyses and scans as appropriate, including but not limited to:
Static Code analysis, 3rd Party Dependencies Vulnerability Scans, Dynamic analysis
3rd Party Dependencies scans - Licenses and Vulnerabilities
Anti-Malware Scans
Issues found go through a triage process and through a remediation process, as necessary.
Following testing and remediation, all UiPath products including official activity packages are code-signed by UiPath to provide authenticity and integrity. Partner and open-source packages included in UiPath offerings also go through the same testing, but are typically code-signed by their respective authoring body.
Security SDLC Tasks implemented as appropriate:
Explore other topics
Privacy
Understand more about how we collect, use, disclose, share, and process data when people visit our website.
Find out moreLegal
Read the UiPath legal terms to find out more about the principles guiding your relationship with UiPath.
Find out moreCompliance
Discover our Global Partner Code of Conduct, our compliance standards, and our certifications and attestations.
Find out moreSubscribe to UiPath Trust Center updates
Receive announcements regarding security advisories, and legal or policy updates.
